Cybersecurity
- 1. Cyber Security A professional approach to protection
- 2. What is Cyber? What is Cyber Security? Elements of Cyber Security Types of Cyber Threats Latest Cyber Threats End-User Protection Cyber Safety Tips
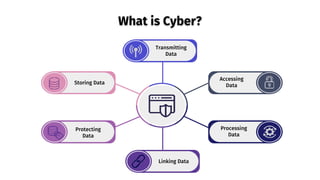
- 3. What is Cyber? Storing Data Protecting Data Accessing Data Processing Data Transmitting Data Linking Data
- 4. What is Cyber Security? Cyber security refers to the body of technologies, processes, and practices designed to protect networks, devices, programs, and data from attack, damage, or unauthorized access. Cyber security may also be referred to as information technology security.
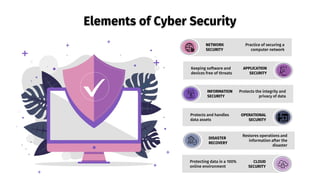
- 5. Elements of Cyber Security NETWORK SECURITY Practice of securing a computer network APPLICATION SECURITY Keeping software and devices free of threats INFORMATION SECURITY Protects the integrity and privacy of data OPERATIONAL SECURITY Protects and handles data assets DISASTER RECOVERY Restores operations and information after the disaster CLOUD SECURITY Protecting data in a 100% online environment
- 6. Types of Cyber Threats Cyber-crime 1 Cyber-attack 2 Cyber-terrorism 3 There are three forms of cyber-threats:
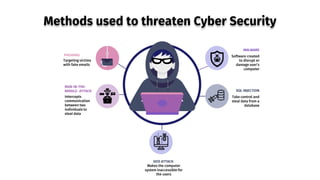
- 7. Methods used to threaten Cyber Security PHISHING Targeting victims with fake emails MALWARE Software created to disrupt or damage user’s computer MAN-IN-THE- MIDDLE- ATTACK Intercepts communication between two individuals to steal data SQL INJECTION Take control and steal data from a database DOS ATTACK Makes the computer system inaccessible for the users
- 8. Latest Cyber Threats DRIDEX MALWARE Affects the public, government, infrastructure and business worldwide SCAM DATING SITES Affects people emotionally and personally EMOTET MALWARE Steals data and load malware
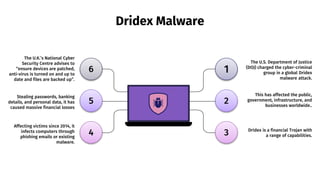
- 9. Dridex Malware The U.S. Department of Justice (DOJ) charged the cyber-criminal group in a global Dridex malware attack. 6 1 2 4 3 5 This has affected the public, government, infrastructure, and businesses worldwide.. Dridex is a financial Trojan with a range of capabilities. Affecting victims since 2014, it infects computers through phishing emails or existing malware. Stealing passwords, banking details, and personal data, it has caused massive financial losses The U.K.’s National Cyber Security Centre advises to “ensure devices are patched, anti-virus is turned on and up to date and files are backed up”.
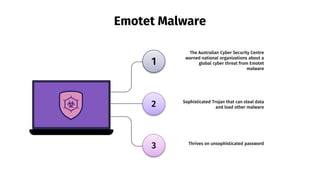
- 10. Emotet Malware The Australian Cyber Security Centre warned national organizations about a global cyber threat from Emotet malware 1 2 3 Sophisticated Trojan that can steal data and load other malware Thrives on unsophisticated password
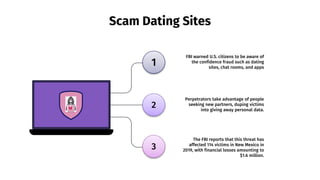
- 11. Scam Dating Sites FBI warned U.S. citizens to be aware of the confidence fraud such as dating sites, chat rooms, and apps 1 2 3 Perpetrators take advantage of people seeking new partners, duping victims into giving away personal data. The FBI reports that this threat has affected 114 victims in New Mexico in 2019, with financial losses amounting to $1.6 million.
- 12. Why Cyber Security is important? Government, Military, corporate world, financial, and medical organizations, collect, process, and store unmatched data on devices. Data can be sensitive information, like intellectual property, financial data, or personal information, and data with negative consequences. Organizations transmit sensitive data across networks and to other devices while doing business. Thus, Cyber Security describes the discipline dedicated to protecting that information and systems that areused to process or store them
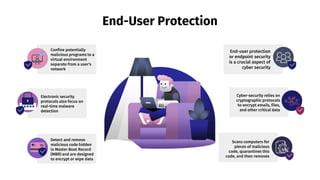
- 13. Detect and remove malicious code hidden in Master Boot Record (MBR) and are designed to encrypt or wipe data End-User Protection End-user protection or endpoint security is a crucial aspect of cyber security Cyber-security relies on cryptographic protocols to encrypt emails, files, and other critical data Scans computers for pieces of malicious code, quarantines this code, and then removes Confine potentially malicious programs to a virtual environment separate from a user's network Electronic security protocols also focus on real-time malware detection
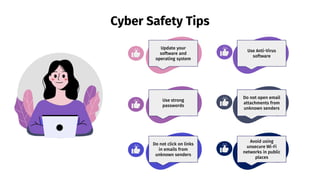
- 14. Cyber Safety Tips Do not open email attachments from unknown senders Avoid using unsecure Wi-Fi networks in public places Use Anti-Virus software Update your software and operating system Use strong passwords Do not click on links in emails from unknown senders